Viber protection mechanisms How to protect Viber from hacking
Messengers, social networks, and all sorts of popular sites constantly talk about the "high level of protection of user data. But periodic hacking of other people's accounts and leaks of personal details of famous people indicate the opposite.

Today I want to talk about how much the developers of Viber take care of the secrecy of our correspondence and how they do it. I will also prove that any methods of protecting accounts in the messenger can be useless if only the phone number of a potential "victim" is used for an attack.
Security mechanisms: how Viber takes care of user privacy
By far the most secure method of protection is end-to-end encryption. That's what Viber claims to use when transmitting data from one user to another. This protection mechanism involves encrypting data on the sender's device, and decrypting received media files, voice or text messages on the recipient's smartphone or PC.
However, this encryption method has a negative impact on user comfort. Therefore, the creators of messengers try to find a compromise between convenience and security. Which, by the way, is practically unattainable. Often, programmers give up some elements of security for the sake of increasing the user's comfort. Naturally, this increases the popularity of the application, but makes it vulnerable to hacker attacks.
Now it's hard to call Viber the most popular messenger, but it is its privacy policy of maximum use of end-to-end encryption algorithms for all participants of any conversation without exception. So what does this mean for users?
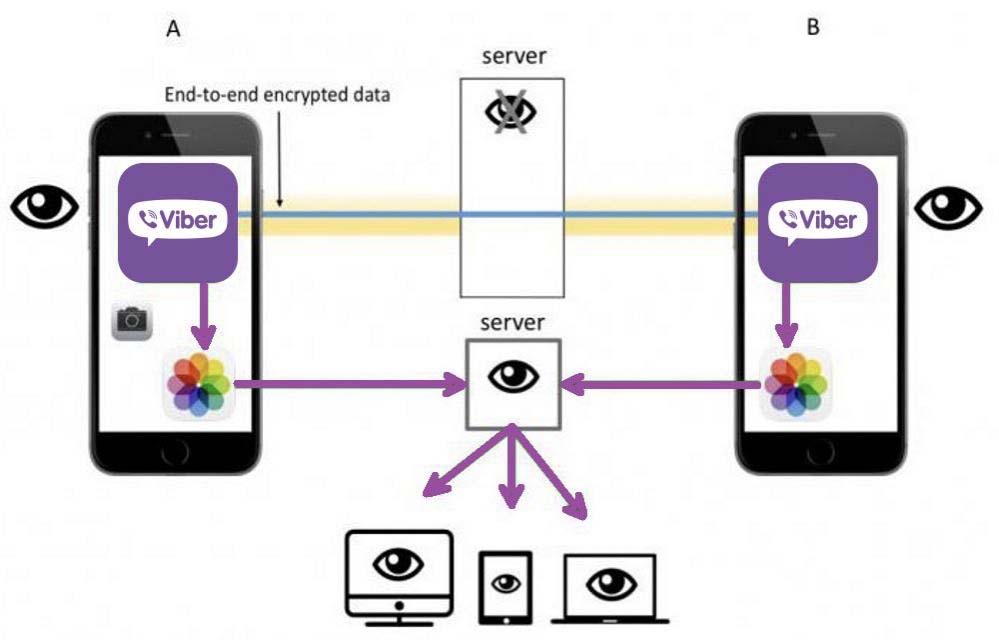
Before starting a dialog, users automatically generate 256-bit keys that include a public and a private part. Public halves are exchanged between chat participants, while private keys encrypt messages on the senders' side. When a text, voice recording, photo or video is received, the messenger matches both parts of the key, and once they match, it decrypts the data. If a user's account is connected to several devices (for example, a tablet and a smartphone), a unique key is generated for each of them.
Messages are always stored in encrypted form on Viber's servers and remain there only until the user logs on. After that, all viewed messages are added to the backup copy, and its current version is sent to the cloud storage on Google Drive (for Android users) or iCloud (for iOS users). This is done so that when you change devices, you can restore your correspondence and get full access to the information saved in Viber.
It is impossible to read someone else's correspondence from the messenger servers (even if you somehow manage to hack them). But bypassing such protection in Viber is quite realistic: you only need to get access to the target account, and from it go to the backup and download it.
Many manuals on using Viber suggest disabling backup and prohibiting messenger access to cloud storage as the main protection mechanism. But such a ban will be in effect until the first update of the system or the application itself, and if you change your phone number or smartphone, it will not allow you to restore correspondence (which will most likely lead to the loss of important information for the user). In addition, the absence of a backup copy will make it possible to use Viber from only one device, as the messages sent by the other gadgets simply will not reach.
As statistics show, almost none of the active users of the messenger do not agree to such inconveniences for the sake of increased security. In addition, all data stored in Google Drive and iCloud are considered by default to be maximally protected from any hacker attacks.
Critical Viber vulnerability
Viber itself has no critical vulnerabilities, i.e. it does not allow for mass hacking attacks on users. In order to hack a certain account, it is necessary to gain access to the device with the target account. And this is quite easy to do, knowing only the phone number of a potential "victim".
It is enough to connect to its mobile network, initiate login to the target account on any other gadget and intercept a message from Viber with a verification code. Now a backup copy of the messenger will be loaded on the new device and will be constantly updated when receiving or sending new messages and making calls.
The main problem of this Viber hacking methods - intercepting a system message from a messenger. But this task is easily handled by specialized software such as VbTracker. It is already configured to connect to any mobile network that uses the SS7 protocol for data transmission. And it is this protocol is used in the transmission of SMS by almost all existing mobile operators.
After the message is intercepted, the program automatically logs into the desired account, downloads the actual backup of user data, and passes it to the person who initiated the attack. All this takes no more than 15 minutes and does not even require any technical knowledge or special skills.
Are there 100% ways to protect your Viber account from hacking
No matter how the developers of the application or you personally try to protect your Viber account from hacking, it can all be completely useless. After all, the main vulnerability of any account is its connection to a phone number. And until mobile operators start making as much effort to preserve subscribers' privacy as the creators of messengers do, your personal data will always be at risk.